 Malta, Knights and Freemasons, a combination that in other times would not have caused a stir but rather the belief that cathedrals were erected by humble stonemasons enslaved to the Knights once Templars, then Knights of Rhodes and finally Knights Hospitallers
Malta, Knights and Freemasons, a combination that in other times would not have caused a stir but rather the belief that cathedrals were erected by humble stonemasons enslaved to the Knights once Templars, then Knights of Rhodes and finally Knights Hospitallers
Malta, little businessman, Knights and Freemasons are nowadays for those who would like to enter the two Institutions, a very difficult goal to reach because to enter the Hospitaller Knights it should be necessary to have the requisites of economic solidity, a real degree and not the ones you buy in Swiss markets or universities for a fee, a noble title or in any case to be honest and good people even if not graduated.
The title of nobility is cited as indispensable to join the Order of the Knights Hospitallers of Malta, but we remind everyone that one inherits it only from one’s father and not from one’s mother by attaching the title of nobility to one’s father’s surname because it is fraudulent, to be one of those people dedicated to good works if they have the financial requirements and not living on gimmicks and subsidies from the State of Malta because no lieutenants or even worse, on gimmicks by boasting non-existent titles in neighbouring countries in order to collect what thousands of euros to survive.
The same is true for those who wish to enter the Institution of Freemasonry, an institution even older than the Knights Templar, where, as also described in the Holy Bible, the Talmud and the Koran (Old Testament), an architect in the service of King Solomon, made available its existence to erect a Temple enslaved by free masons (the ancient stonemasons) and later the same institution first made itself available to the Knights Templar and then later passed into the service of the various knightly orders that today boast of Malta.
The beautiful cathedrals, but above all the walls of the ancient defence of the three castles of Valletta still bear the tangible signs of the Freemasons (rock and stone workers) who actively participated in the realization of works still present today and whose wonders are the pride of the island of Malta.
But of all this history, as always, the Holy Roman Church, which should only be a shepherd of souls and not enslaved to vice, to money, to subjugate Catholic populations because we are no longer at the time when the Pope had power of life and death over his subjects, with to this day, the apologies to the Catholics by successive Popes, still exerts a strong and close influence on the Maltese population and on Malta itself.
The Freemasons in Italy, are legally recognized as a result of respect for the Anselmi law, which prevents anyone from operating in secret and imposes that every Freemason, Masonic association and/or Masonic Obedience self-declaration at the Prefecture, notifying the Ministry of the Interior so that it can be demonstrated that they are not affiliated with Mafia gangs, but that they are transparent and legal in accordance with the laws of the State.
The laws of all the Republican States that call themselves democratic, grant freedom of worship, freedom of speech, freedom of race so that no one can feel the victim of persecution and they are all countries that fortunately belong to Europe and to many other prestigious nations such as the United States of America, Australia and so on, apart from totalitarian countries where even the professing of a religion becomes an object of crime.
The Freemasons embrace as brothers the Muslims, the Jews, the Catholics and bow before the three sacred books without any constraint, but with spontaneity and sincere heart on a par with the Knights of Malta, They question the impositions of the Holy Roman Church that still carries out in the 21st century, interference due to the denial of the archaeological and scientific discoveries that undermine the New Testament and not the respect for the Old Testament that we can find in all three sacred books of primary monotheistic religions.
This is the only difference between the Knights Hospitallers of Malta and the Freemasons, the former accept the interference of the Holy Roman Church and the Freemasons question them democratically and freely while respecting the teachings of the Old Testament and bending over the Churches in front of the altars marking themselves with the cross before the figure of Christ, bowing before the Talmud and bowing in prayer in respect of the Koran.
Today we will tell you a fairy tale, close to what may have been the reality for a little businessman who, as a Freemason, had never missed the teachings of his religious and Institutional Creed and thought he was still living in the past, where respect for the Knights was an ordinary thing and above all believing in their words that they should have been sincere and come out of a pure heart, a fairy tale of our days very relevant to the Knight.
Today we are going to tell you a fairy tale, close to what may have been the reality for a little businessman who, as a Freemason, had never missed the teachings of his religious and Institutional Creed and thought he was still living in the past, where respect for the Knights was an ordinary thing and above all believing in their words that they should have been sincere and come out of a pure heart, a fairy tale of the present day very relevant to the Knights Hospitallers of Malta, the Freemasons and the intrigues that host the most vile figures in this fairy tale told in a modern key.
But let us remember, though a fable of fantasy that does not want to offend anyone or besmirch the honour of any institution and is the fruit of freedom of thought and freedom of speech, but still a fable that could also be reflected with reality and the key to interpretation, each of us can give it to ourselves thinking of Malta, Knights and Freemasons.
One day, a small computer entrepreneur and Freemason who was beginning to approach the internationalization of companies, the registration of companies abroad and was fascinated by the financial world that could help and unblock the financial problems of many companies in difficulty but with interesting projects, came into contact with a person who professed to be a Knight and said he was a lawyer and doctor because he belonged to a noble family.
The two, began to feel more and more often and the little businessman began to open up and trust the Knight mindful that the latter, by oath, could never hurt him but rather, with his sword could offer him protection in a new world of which the Knight had always spoken to him showing him a world where true freedom and democracy was common practice and that the island was not a dream but a true Earthly Paradise of justice and mutual respect.
Malta, Knights and Freemasons, where the little businessman pointed out to the Knight that he was not rich but a hard worker, esteemed by many people because he was honest and that he was approaching the financial world fearfully so as not to make mistakes but, he was not in a position to leave his country if he did not have the opportunity to work and support himself by moving to the island of his dreams.
The Horseman, strong of his boastful titles that later turned out to be all fake, made him meet with someone he called a great mussel farmer, yes, you understand correctly, a mussel farmer who had a big company and was very rich and would have liked to be able to open a company in the paradise island by making it run by an honest person of trust.
The Knight convinced the little businessman to trust him and made him get an honest contract that would allow him to live normally on the island and take care of the business of the big mussel farmer who first wanted a bar and restaurant and then changed his mind and wanted to become an established manager for a bed & breakfast.
The little businessman, he let himself be convinced and left his homeland strong of a good contract and the word of the great mussels entrepreneur, who should never have regretted the choice because the Knight was also a lawyer (bogus by title) of his big company and nothing could endanger his future.
Arrived on the island paradise, the little businessman began to respect all the points of the contract under the direct control of the Knight and an accountant who was responsible for the respect of the contract and when he began to turn the island to set up the bed & breakfast he heard that the great mussels entrepreneur could not spend 800,000 euros for a structure with legal concessions but, having an apartment for rent, he would have liked to rent the beds and so on by renting other properties but making a crime to the little businessman who refused.
The poor little businessman looked and hoped for the wisdom of the Knight and began to doubt who he was and, as a good Mason, asked questions to other Freemason brothers who were hiding on the island and in his country of origin, discovering that the great mussel businessman was nothing but a scoundrel who had taken advantage of his good faith and who, having been discovered, had suspended the payment of his quarterly debt.
The Knight that the little businessman admired, was none other than a braggart who pretended to be noble but who had nothing noble but a mountain of lies, that the Knight was not a lawyer but that he had given 1 (one) only examination in jurisprudence and that he was not accredited to any legal order neither in his country of origin, nor in the island nor in the neighbouring countries, that the Knight had also lied about his profession as a doctor because he was not a doctor but had been a nurse in a clinic on the island in the past and that he had resigned saying that he wanted to enrich himself with business then imaginary or small results and that he lived by getting paid for bogus advice thanks to the false references he gave in the country of origin of the little businessman.
Malta, Knights and Freemasons, where the little businessman felt he was dying and had another small heart attack, where among tears and praying like a good Catholic, he told his wife to take him back to his country because that was where he wanted to die, yes, because in the past he had had three of great importance that had led him almost to leave his loved ones to reach the God.
The discoveries that he had made had destroyed him and he was afraid for the survival of his family and his children, he had brought them to the island and he wondered how he could live since he had closed all the old contracts to honor the one with the great mussel contractor.
He cried in the silence of the night, he felt himself dying for the fate that could touch his children and his wife and icing on the cake, one fine day, the little businessman, on the phone with the great mussel entrepreneur, who gave money for no reason whatsoever to the Knight, told him that the Knight was not who he said he was and that he was not a “c…o” of noble but a boaster and that he would have done well to look at him too and above all, to be honest with his wife and confess to her all the handouts made.
The little businessman had not yet understood that the large mussel entrepreneur was in cahoots with the Knight and that he would later blackmail him with more than one email and whatsapp messages, writing him that he had recorded the phone call and attempted extortion by saying that the Knight, his lawyer, had told him that the business of the little businessman who regularly paid taxes to the British crown was fake and that he wanted money.
The little businessman was surrounded by a gang of thugs and since he had not paid the extortion, he heard from a brother in Freemason’s sleep and presented himself as a government, that the Knight had gone to him and told him that the poor little businessman had tried and made money laundering and that he was in a position to ruin him if it was true.
The little businessman handed over all the papers of his British company and all his email correspondence, as well as all the whatsapp conversations he had with the Knight and the great mussel entrepreneur, handed over all his personal and corporate statements to prove that he was a man of good morals, an honest person who tried to work honestly in compliance with all international laws.
The Government or the one who still thought he was, after due diligence and after seeing that the little businessman was an honest man and that he had promptly proved it to him within ten minutes by handing everything over to him by email, when he heard the little businessman ask for justice because he had been falsely accused of a serious crime he had never committed, he simply replied that he wanted to stay out of it and that he did not want to be involved in it… a real coward, nothing but a sleeping Freemason brother.
The Horseman, threatened the little businessman two days later, telling him that he would even take the Vatican police as well as the police of the island to his home, but the little businessman who had nothing to hide because in the meantime he had already warned his lawyers in his country and the Freemasons brothers of the island who are forced to hide for fear of retaliation by religious and government bodies and the Freemasons brothers of his home country and Great Britain where the top of Freemasonry is the most important figure in the world, did not compromise and did not take an interest in the threats of the Knight.
At that point, he turned to the superior of the Knights asking to be put before the Masonic tribunal in conjunction with the tribunal of the Knights for justice, but since the Knight had created a false knightly order in the country of origin of the little businessman, with the help of a former Senator of the State of the little businessman, the superior of the Knights told him that nothing was in his power but to give him moral support as he should to a brother who had suffered so many wrongs.
The little businessman, in order to save his family more than himself, and fearing for the safety of his loved ones, since the Knight also had deep roots in an island of the Country where the little businessman came from but where the Mafia had always been the boss, decided to return immediately to his country by making himself available to his competent authorities and talking to a representative of his State.
The little businessman never gave in to blackmail, extortion, attempts to intimidate the Mafia that he had suffered on the island, but when he returned to his own country, he began again in small steps in the slow recovery he and his family turning to the authorities who, investigating, would then find a diplomatic incident in his stories and above all proven what he had told.
The Horseman, the great mussel entrepreneur, thought that everything had been solved with the silence of the little businessman who, instead, was asking the British State to investigate the blackmail and attempted extortion perpetrated against him as Director of an English company.
Too bad only that the accountant and superior of the Knight, at first he had listened and comforted his brother as true knights do, then, it is not understood for what reason, he started to move away and then disappear into thin air with the regret and displeasure of the little businessman.
And as one would say in such cases: This fairy tale has not yet had a negative outcome, nor a positive epilogue, but the ending is still to be written and above all, we would like to remind the Freemasons who is in charge of Freemasonry in Great Britain and that no one can be above the laws of a state governed by law or must be forced to hide because he is a Freemason.
We only hope that this will be understood as a fairy tale and that no one will ever have to end up like the sad journalist Daphne Caruana Galizia as they had let the little businessman understand.
We, always remembering that this is a fairy tale and therefore an expression of fantasy, are to remind everyone that “Any reference to existing people and places or to facts that really happened is purely random” and nothing can be linked to Malta, Knights and Freemasons.
ADT London 25 January 2020
 Online scams have become very profitable for phantom companies, and an asiatic State, as always, is the master, since although it can boast of very serious and reliable companies, it proves to have no control bodies to search online for its compatriots who play with the lives of companies and people by carrying out all kinds of commercial crimes, especially in the name of companies that have never had business relations with them and are completely unaware of what is happening
Online scams have become very profitable for phantom companies, and an asiatic State, as always, is the master, since although it can boast of very serious and reliable companies, it proves to have no control bodies to search online for its compatriots who play with the lives of companies and people by carrying out all kinds of commercial crimes, especially in the name of companies that have never had business relations with them and are completely unaware of what is happening



 Ecommerce in Malta, a system related to online sales that we can assure you, works perfectly without creating problems for either sellers or buyers, in spite of what many exclusively Italian and German journalistic sources try in every way to discredit because obviously, they have to pull the water to their own mill
Ecommerce in Malta, a system related to online sales that we can assure you, works perfectly without creating problems for either sellers or buyers, in spite of what many exclusively Italian and German journalistic sources try in every way to discredit because obviously, they have to pull the water to their own mill









 Refurbished Computers for businesses and professionals, certainly allow you to save up to 60% compared to the price of a new product of equal performance
Refurbished Computers for businesses and professionals, certainly allow you to save up to 60% compared to the price of a new product of equal performance


 All refurbished computers are connected to our internal network during testing, which uses standard DHCP in order to fully upgrade operating systems before the final test.
All refurbished computers are connected to our internal network during testing, which uses standard DHCP in order to fully upgrade operating systems before the final test.

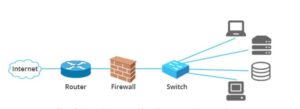
 Los mini-PCs sin ventilador son geniales para este propósito ya que son pequeños, silenciosos, eficientes energéticamente y tienen de 2 a 6 puertos Ethernet en ellos soportando brillantemente el ROUTER FIREWALL OPNSENSE, y necesitarás
Los mini-PCs sin ventilador son geniales para este propósito ya que son pequeños, silenciosos, eficientes energéticamente y tienen de 2 a 6 puertos Ethernet en ellos soportando brillantemente el ROUTER FIREWALL OPNSENSE, y necesitarás
 TECHNICAL ASSISTANCE is taken care of by the SHADOIT CONSULTANCY GROUP and is interested in computer structures with professionalism and twenty years of experience gained by its technicians from various large companies
TECHNICAL ASSISTANCE is taken care of by the SHADOIT CONSULTANCY GROUP and is interested in computer structures with professionalism and twenty years of experience gained by its technicians from various large companies

 SECURE OS TOR a perfect operating system for USB sticks, where IT security technicians have always followed the course of events
SECURE OS TOR a perfect operating system for USB sticks, where IT security technicians have always followed the course of events
 istent s
istent s





 Malta, Knights and Freemasons, a combination that in other times would not have caused a stir but rather the belief that cathedrals were erected by humble stonemasons enslaved to the Knights once Templars, then Knights of Rhodes and finally Knights Hospitallers
Malta, Knights and Freemasons, a combination that in other times would not have caused a stir but rather the belief that cathedrals were erected by humble stonemasons enslaved to the Knights once Templars, then Knights of Rhodes and finally Knights Hospitallers Loss of work, a serious social problem that is crossing Europe, but above all an Italy brought to its knees by a Christian Democrat past that has only known how to put this country in debt for the next generations and that has led with the new governments only to be more alone, closed in its miseries and its sadness hidden from the world and that no one cares about it
Loss of work, a serious social problem that is crossing Europe, but above all an Italy brought to its knees by a Christian Democrat past that has only known how to put this country in debt for the next generations and that has led with the new governments only to be more alone, closed in its miseries and its sadness hidden from the world and that no one cares about it  Qatar 2022 or should we say Welcome Qatar, but not in prehistory, but in a modern era that should take us to a civilized country of the 21st century for the next World Cup announced with such clamor by FIFA
Qatar 2022 or should we say Welcome Qatar, but not in prehistory, but in a modern era that should take us to a civilized country of the 21st century for the next World Cup announced with such clamor by FIFA 